A recent boom in advanced tech is revolutionizing building security management by making processes more efficient & affordable. Learn more.
 Blogs
Blogs 
 Blogs
Blogs A recent boom in advanced tech is revolutionizing building security management by making processes more efficient & affordable. Learn more.
 Guides
Guides According to a recent report released by the Security Industry Association (SIA), artificial intelligence is #1 on the list of trends expected to define physical security in 2021. But how can technology like AI serve to improve physical security? Read on to learn more.
 Guides
Guides This guide provides information on how a “smart” video surveillance system is architected, its capabilities and limitations, and the trade-offs of processing the analytics on the cloud vs. on-premise.
 Case Studies
Case Studies Read Actuate’s Genesis case study to learn how our AI software offered the most desirable solution to the company’s growing security challenges.
 Guides
Guides Actuate’s Construction Site Security Guide offers insights into the most common risk factors and best practices. Learn how through proper due diligence and planning, contractors can successfully mitigate and prevent the risk of theft.
 Case Studies
Case Studies Actuate’s technology turned the existing security cameras at St John into intruder and gun-detecting smart cameras, enabling instant, real-time responses.
 Guides
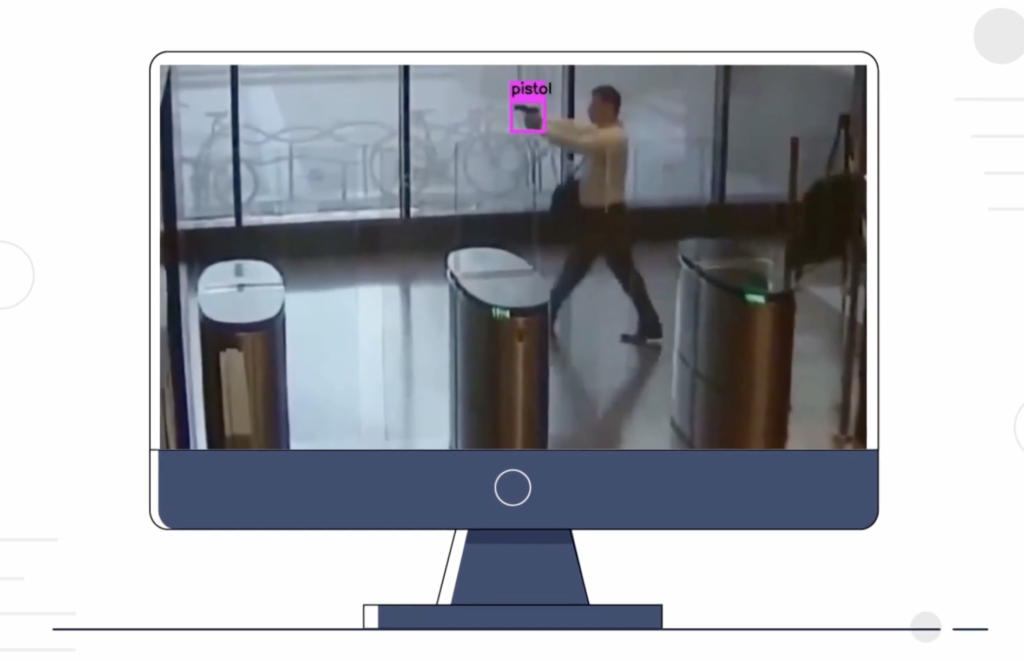
Guides Actuate’s real-time weapon detection system turns any security camera into a gun-detecting smart camera. Get the briefing to understand how Actuate can help your organization.
 Guides
Guides The Actuate AI system effectively protects facilities by detecting intruders using existing security cameras, eliminating the need for new hardware. Because it’s based on the latest deep learning AI technology, false positives are eliminated.
 Guides
Guides While Actuate is compatible with almost any security camera system, it works best when used with a Video Management System (VMS). Learn which VMSes Actuate is compatible with here.
 Guides
Guides Actuate provides real-time intelligence about the location, identify, and armament of the shooter through integrations with top Video Management Systems, giving security and law enforcement the tools they need to dramatically reduce response times.
 Guides
Guides Next-generation physical security applications have high performance requirements that on-premise hardware struggles to meet. Cloud deployments are the solution to improving building security with new technology while reducing costs.
 Guides
Guides By using existing, IT-approved security hardware and software, minimizing data retention, and leveraging world-class cybersecurity platforms, Actuate is compliant with IT and Privacy policies.